Why Iran’s nuclear facilities are still vulnerable to attack
 EPA
EPAThe end of the Trump era has caused a collective but cautious sigh of relief in Iran.
Some in the Gulf region feared that in the dying days of his presidency Donald Trump might choose to double down on his policy of "maximum pressure" on Iran and launch a military strike on its civilian nuclear plants and other targets.
Reports from Washington in November indicated this was one option the US president had looked at, before being talked out of it by his advisers.
By contrast, President-elect Joe Biden has made it clear that he wants the US to rejoin the 2015 nuclear pact with Iran, which would mean reversing sanctions and releasing money to Tehran in exchange for Iran's full compliance.
So is Iran now safe from attack?
 AFP
AFPIn a word, no. Israel remains extremely concerned, not just by Iran's civilian nuclear activities but by its prolific programme to develop its arsenal of ballistic missiles.
On Thursday, Israel's Defence Minister Benny Gantz was quoted as saying, in reference to Iran's nuclear development programme: "It is clear that Israel needs to have a military option on the table. It requires resources and investment and I am working to make that happen."
Israel, as the Islamic Republic's declared enemy, sees a nuclear bomb in Iranian hands as a threat to its very existence and has urged the world to stop it before it is too late.
Iran has always insisted its nuclear programme is purely peaceful, but its recent action to increase the enrichment of its uranium - one of a sequence which contravene the 2015 deal - has set alarm bells ringing.
In 1981, Israel suspected that Iraqi President Saddam Hussein was looking to acquire a nuclear weapons capability.
In Operation Babylon, it took pre-emptive action by carrying out a successful air raid using its own F15 and F16 jets, destroying Iraq's Osirak nuclear reactor.
Twenty-six years later, in 2007, it did the same to Syria in Operation Outside the Box, destroying a secret plutonium reactor in the desert near Deir al-Zour just before it was activated.
Out of sight
But Iran is a far harder target, in terms of distance, accessibility and air defences.
It is questionable whether Israel could carry out a successful air raid without US participation - something a Biden administration will be reluctant to do.
 Maxar Technologies via Getty Images
Maxar Technologies via Getty ImagesConscious of the longstanding threat to its nuclear facilities - from the US, Israel and possibly the Gulf Arab states - Iran has invested money and effort in burying some of them deep underground, beneath its mountains.
Iran's nuclear industry, while ostensibly civilian, is closely entwined with its military and security infrastructure.
In fact, the Iranians have had so long to prepare for an attack that there is now a distinct possibility that their underground facilities are becoming impenetrable.
Despite this, Iran's nuclear facilities remain vulnerable to attack on three fronts.
Physical attack
"Iran's facilities are not impregnable," says Mark Fitzpatrick, an associate fellow at the International Institute for Strategic Studies (IISS) and an expert on arms control.
"[The one at] Natanz is vulnerable to precise bunker-busting bombing, maybe taking two precise hits: one to dig a crater and the other to burst through it or at least to shake the delicate machines enough to put them out of commission."
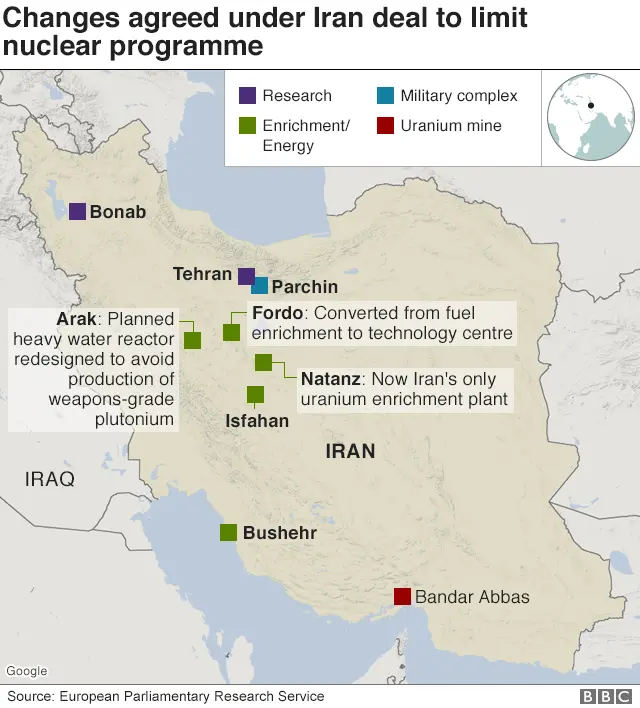

But Iran is a vast country and its nuclear facilities are spread out in depth.
As far back as 2012 experts suggested that the uranium enrichment facility at Fordo, buried at least 80m (260ft) inside a mountain, might be impregnable to even the devastating explosive power of US "bunker-busting" precision-guided bombs.
"Fordo's greater depth protects the facility against bunker-busters, but not against sabotage," says Mark Fitzpatrick, "and it could be put out of commission for a period of months by blasting its entryways and airshafts".
 GeoEye Satellite Image
GeoEye Satellite ImageBut to reach these facilities would require one, possibly two waves of air strikes penetrating deep into Iranian airspace and either evading or overpowering its air defences.
Iran has invested heavily in developing its surface-to-air missile force, including the Bavar-373 - a homegrown version of Russia's S-300 system that is capable of tracking and shooting down aircraft up to 300km (186 miles) away.
The prospect of an only partially successful strike, with downed pilots captured and paraded on Iranian TV, is a strong disincentive.
Human attack
This has already been happening.
Israel's Mossad intelligence agency has managed to develop an extraordinarily well-informed network of agents inside Iran.
So well-informed that when Iran's top military scientist, Brig Gen Mohsen Fakhrizadeh, was travelling in a protected convoy on a lonely road east of Tehran on 27 November his attackers knew his precise route and timings.
 Reuters
ReutersReports differ on how he was attacked on that day.
Iran claims it was by a remote, satellite-controlled machine gun mounted on a pick-up truck. Other sources believe it was by a sizable team of Mossad-trained agents, who escaped and remain at large.
Either way, Fakhrizadeh - known as "the godfather of Iran's nuclear programme", who US intelligence says carried out covert work on nuclear weapons - was assassinated.
Israel has not commented officially on who was behind it.
Before that, between 2010 and 2012, four leading Iranian nuclear scientists were all assassinated inside Iran, some by car bombs.
Again, Israel neither confirmed nor denied its involvement. But the killings show that despite heavy protection by Iranian state security, assassins are able to reach their targets, setting back Iran's intellectual capacity in nuclear technology.
Cyber attack
There is an undeclared war going on in cyberspace, with Iran on one side and the US, Israel and Saudi Arabia ranged against it.
In 2010, a sophisticated piece of malware codenamed Stuxnet was secretly introduced into the computers controlling Iran's uranium-enriching centrifuges at Natanz.
The result was chaos, causing the centrifuges to spin out of control and setting the enrichment programme back by years.
 Reuters
ReutersThe cyber attack was widely reported to have been Israeli, although US and Israeli experts are believed to have collaborated on developing Stuxnet.
Iran soon hit back, successfully inserting its own sophisticated malware codenamed Shamoon into the network of Saudi Arabia's state-owned oil company, Saudi Aramco, disabling 30,000 computers and threatening Saudi Arabia's oil production.
Further attacks have followed.
Continual risk
The 2015 nuclear deal - the Joint Comprehensive Plan of Action - was supposed to place such stringent curbs on Iran's nuclear activities that it would negate the need for its adversaries to consider a military strike.
 EPA
EPABut Israel and Saudi Arabia were always sceptical about the deal because they considered it too lenient and temporary, and because it did nothing to address Iran's ballistic missile programme.
Today, they are less than enthusiastic about a Biden presidency reviving the deal unless it addresses those concerns.
Nobody in the Gulf region wants to see another conflict. Even the 2019 missile attack on Saudi Arabia's oil infrastructure, widely blamed on Iran and its allies, went unanswered.
But as long as suspicions remain that Iran is secretly working on developing a nuclear warhead capability, then the risk of a pre-emptive attack on its facilities will always be there.
